Addressing the Data Breach Crisis: Comprehensive Solutions for a Safer Digital World
Every 39 seconds, there’s a cyber-attack! The ramifications are significant.
Impact: Loss of trust, damage to reputation, and significant fines.
Data breaches can cripple an organization’s future. There is often an immediate financial fallout, but the continuing effect of cyber attacks ripple far beyond.
We’re facing a serious data breach crisis, and advancements in AI will only cause this problem to get more serious.
Learn how to protect your organization against a data breach in 2023 and 2024!

The Daunting Reality of Data Breaches
Recent Epidemic: The 2023 Data Breach Surge
The digital landscape of 2023 is marked by an alarming surge in data breaches. With the ubiquity of cyber-attacks, businesses are in a perpetual battle to protect their digital assets. The aftermath of a breach is multifaceted: tarnished reputations, dwindling trust, and punitive fines.
Amidst this chaos, the rise of artificial intelligence amplifies the challenges. Organizations must stay vigilant, equipping themselves with the latest countermeasures and strategies, ensuring not only their survival but also their growth in this treacherous digital terrain.
 Implications for Stakeholders
Implications for Stakeholders
Financial Fallout: A single breach can result in an average loss of $3.86 million for businesses. Yet, it’s not just about the money. A data breach can tarnish a company’s reputation for years, making recovery a long, uphill battle.
For Health Organizations or those under HIPAA standards, the U.S. Department of Health and Human Services maintains a list of breaches of protected health information affecting 500+ individuals. I personally checked and found it here. If you’re interested in breaches from August and September 2023, you’ll find them at the bottom of this blog post.
There are a plethora of resources to help your company protect itself against a data breach. Here, you’ll find plenty of guidance and a list of resources as well.
While large organizations have the biggest risk, individuals aren’t safe either.
Personal Impact: For individuals, the implications are equally dire: stolen identities, credit fraud, and personal information landing in the wrong hands. There’s a looming sense of violation, a piercing of personal security that’s truly unsettling.
Deciphering the Myths
The False Comfort of Advanced Software
One of the most widespread myths? “We’ve got the latest security software, so we’re safe.” Sadly, even the most advanced software can’t always protect against human error or determined hackers. It’s a comforting illusion, but reliance on tech alone is like building a fortress with a hidden backdoor.
Tracing Back: Where Are We Going Wrong?
The Peril of Outdated Infrastructure
Legacy systems—those clunky, old-school computers and servers—are prime targets for hackers. Their outdated security measures are child’s play for today’s sophisticated cyber attackers. And yet, companies hang onto them, as if they’re vintage collectibles rather than ticking time bombs.
Human Missteps
Training as a Necessity: A simple click on a malicious link by an uninformed employee can jeopardize the entire company’s data. Regular training is not just advisable; it’s crucial. The human mind, after all, can sometimes be more porous than any firewall.
 Digital Expansion: A Double-Edged Sword
Digital Expansion: A Double-Edged Sword
The Internet of Things (IoT) and cloud infrastructures amplify the advantages of connectivity. Yet, they also increase entry points for cyber adversaries. We’re sailing swiftly into the digital age, often without a compass.
I remember the early days of the internet, a simpler time when connectivity was a luxury and not the backbone of our daily lives. As we’ve progressed, the digital landscape has expanded exponentially. The allure of smart devices, from refrigerators that can order groceries to thermostats that learn our preferences, has transformed our world. But with this convenience comes a cost.
Every device we add to our network, every application we download, and every cloud service we employ increases our digital footprint. This expansion, while offering unparalleled convenience and efficiency, also broadens the attack surface for potential cyber threats. It’s akin to building more doors in a fortress; while they offer more ways to enter and exit, they also present more opportunities for invaders to breach.
It’s crucial, now more than ever, to ensure that as we embrace the digital age, we do so with a keen eye on security. The seas may be turbulent, but with the right navigation tools, we can chart a safe course.
Unearthing Robust Solutions
 1. The Shield of Data Backups
1. The Shield of Data Backups
Always have a plan B! Regular backups ensure that in case of data breaches, the information isn’t lost forever. Think of it as an insurance policy; you hope you’ll never need it, but you’ll be eternally grateful if you do.
- Frequency Matters: Regularly schedule automated backups, daily if possible, to minimize data loss in the event of an attack.
- Off-Site Storage: Store backups off-site to safeguard against physical disasters like fires or floods that could destroy both primary and backup data.
- Test Restores: Regularly test the restoration process to ensure your backups are functional and can be easily recovered.
2. Guarding Secrets with Encryption
- When data is encrypted, even if hackers access it, deciphering the content is near impossible. It’s like handing over a diary written in an indecipherable language.
- End-to-End Encryption: Implement end-to-end encryption for data both at rest and in transit to ensure comprehensive protection.
- Key Management: Properly manage encryption keys to prevent unauthorized access, and regularly rotate them for added security.
- 3. The MFA Defense
A password isn’t enough. Multi-Factor Authentication (MFA) ensures that even if passwords are compromised, there’s an additional layer of security. Think of MFA as the extra deadbolts on your front door – pesky for intruders, but reassuring for you.
Enable MFA Everywhere: Implement MFA for all user accounts, especially those with access to sensitive data or systems.
Biometric Authentication: Where possible, use biometric authentication methods like fingerprints or facial recognition for added security.
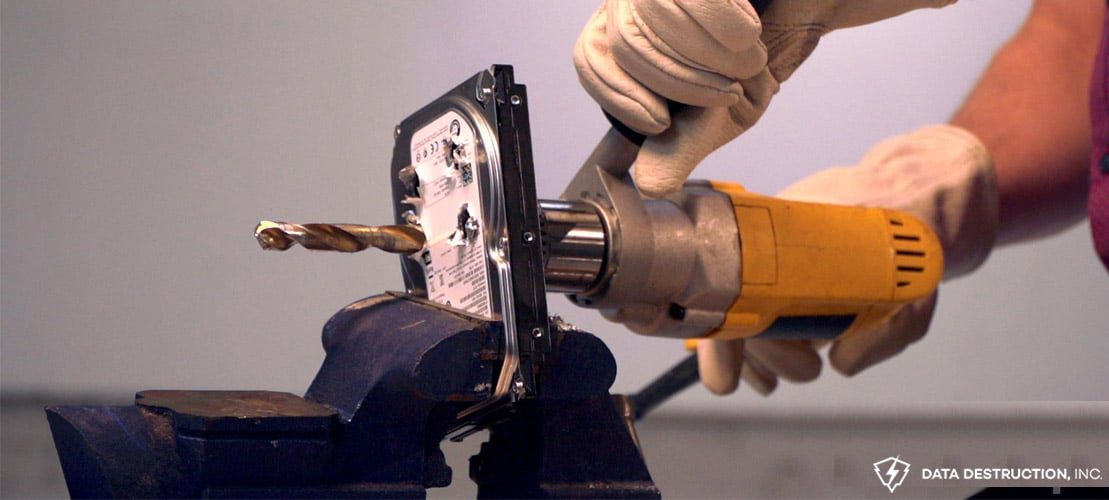
4. Proper Disposal: The Art of Hard Drive Shredding
Old data storage that’s carelessly discarded can be a goldmine for hackers. On-site hard drive shredding ensures old data is eradicated, leaving no traces. Sometimes, destruction is the purest form of protection.
Certified Shredding Services: Engage certified and reputable shredding services from a certified data destruction company to ensure compliance with data protection regulations.
Inventory Tracking: Maintain an inventory of all storage devices, and ensure each one is securely disposed of when no longer needed.
5. Education: The Unyielding Armor
Continuous security training sessions equip employees with the knowledge to ward off potential threats. It’s like sharpening a blade; the better the edge, the cleaner the cut against cyber menaces.
Phishing Simulations: Conduct regular phishing simulations to train employees in recognizing and avoiding phishing attempts.
Incident Response Drills: Practice incident response scenarios to ensure everyone knows their roles in case of a breach.
6. System Health Checks
Regular upgrades and patching of systems ensure you’re always ahead of potential vulnerabilities. This isn’t just maintenance; it’s digital hygiene, as essential as washing your hands in a flu season.
Patch Management: Implement a robust patch management system to keep all software and systems up to date.
Vulnerability Scanning: Regularly scan your network and systems for vulnerabilities and prioritize their remediation.
7. Ready, Set, Defend: Incident Response Plans
In the unfortunate event of a breach, having a plan ensures minimal damage and rapid recovery. Preparedness can be the difference between a stumble and a catastrophic fall.
Incident Response Team: Establish a dedicated incident response team with clear roles and responsibilities.
Communication Strategy: Develop a communication plan to inform stakeholders, customers, and authorities when a breach occurs.
 Overcoming Data Security Hurdles
Overcoming Data Security Hurdles
The Cost Perspective
Consider this: The average cost of a data breach in 2023 is $3.86 million. Investing in robust security measures is significantly cheaper in the long run. Penny wise can mean pound foolish in the realm of cyber threats.
Cost-Benefit Analysis: Evaluate the potential cost of a breach against the investment in cybersecurity measures to make informed decisions.
Size Doesn’t Matter
Small businesses account for 43% of all cyber-attacks. No organization is too small to be on a hacker’s radar. Giants might make bigger splashes
The Rate of Medical Data Breaches is Soaring
For Health Organizations or those who are held to HIPAA standards, the implications are even bigger. The U.S. Department of Health and Human Services, Office for Civil Rights maintains a list of all incidents of breaches of unsecured protected health information affecting 500 or more individuals. Section 13402(e)(4) of the HITECH Act requires that all such incidents be reported. Over the last 24 months, there are a total of 895 such breaches listed on HHS Breach Portal.
In Just August 2023 and September 2023 alone, there have been a total of 67 reported breaches. Here’s a summarized list of these recent breaches:
| Organization | State | Entity Type | Individuals Affected | Date Reported | Incident Type | Affected System |
|---|---|---|---|---|---|---|
| Allegheny County, Pennsylvania | PA | Business Associate | 1,505 | 09/22/2023 | Hacking/IT Incident | Network Server |
| Blue Cross Blue Shield of Texas | IL | Business Associate | 3,708 | 09/22/2023 | Unauthorized Access/Disclosure | Paper/Films |
| Clover Health LLC | NJ | Health Plan | 2,834 | 09/22/2023 | Unauthorized Access/Disclosure | Network Server |
| Health First, Inc. | FL | Healthcare Provider | 14,171 | 09/22/2023 | Hacking/IT Incident | |
| Lakeview Clinic | MN | Healthcare Provider | 624 | 09/21/2023 | Unauthorized Access/Disclosure | |
| Arkansas Total Care, Inc. | AR | Health Plan | 578 | 09/21/2023 | Hacking/IT Incident | Network Server |
| Virginia Dept. of Medical Assistance Services | VA | Health Plan | 1,229,333 | 09/18/2023 | Hacking/IT Incident | Network Server |
| Erlanger Health, Inc. | TN | Healthcare Provider | 2,753 | 09/18/2023 | Hacking/IT Incident | Other |
| Nuance Communications, Inc. | MA | Business Associate | 1,225,054 | 09/15/2023 | Hacking/IT Incident | Network Server |
| Oak Valley Hospital District | CA | Healthcare Provider | 283,629 | 09/15/2023 | Hacking/IT Incident | Network Server |
| Peach State Health Plan | GA | Health Plan | 1,246 | 09/15/2023 | Hacking/IT Incident | Network Server |
| VA Dept. of Medical Assistance Services | VA | Health Plan | 928 | 09/14/2023 | Hacking/IT Incident | Network Server |
| Pharm-Pacc Corporation | FL | Business Associate | 3,749 | 09/12/2023 | Hacking/IT Incident | Network Server |
| Sutter North Surgery Center | CA | Healthcare Provider | 861 | 09/08/2023 | Hacking/IT Incident | Network Server |
| Laboratory Corporation of America Holdings dba LabCorp | NC | Healthcare Provider | 1,431 | 09/08/2023 | Unauthorized Access/Disclosure | Other |
| Ryders Health Management LLC | CT | Healthcare Provider | 7,252 | 09/07/2023 | Hacking/IT Incident | Network Server |
| United Healthcare Services, Inc. Single Affiliated Covered Entity | CT | Health Plan | 315,915 | 09/07/2023 | Unauthorized Access/Disclosure | Network Server, Other |
| Roseman University of Health Sciences | NV | Healthcare Provider | 4,622 | 09/06/2023 | Hacking/IT Incident | Network Server |
| Amerita | KS | Healthcare Provider | 219,707 | 09/05/2023 | Hacking/IT Incident | Network Server |
| Delta Dental of California | CA | Health Plan | 501 | 09/05/2023 | Hacking/IT Incident | Network Server |
| Bienville Orthopaedic Specialists LLC | MS | Healthcare Provider | 242,986 | 09/05/2023 | Hacking/IT Incident | Network Server |
| Bloom Health Centers | MD | Healthcare Provider | 1,545 | 09/01/2023 | Unauthorized Access/Disclosure | |
| North Mississippi Medical Center, Inc. | MS | Healthcare Provider | 950 | 09/01/2023 | Hacking/IT Incident | |
| MedMinder Systems, Inc. | MA | Healthcare Provider | 12,146 | 09/01/2023 | Hacking/IT Incident | Network Server |
| Enzo Clinical Labs, Inc. | NY | Healthcare Provider | 1,700 | 08/31/2023 | Hacking/IT Incident | Network Server |
| Mountain View Family Practice, PC | MA | Healthcare Provider | 5,139 | 08/31/2023 | Hacking/IT Incident | Electronic Medical Record, Network Server |
| Indiana University Health | IN | Health Plan | 1,191 | 08/31/2023 | Hacking/IT Incident | Network Server |
| TTEC Healthcare Solutions | CO | Business Associate | 2,953 | 08/30/2023 | Unauthorized Access/Disclosure | Other |
| O’Neil Digital Solutions, LLC | CA | Business Associate | 1,722 | 08/30/2023 | Unauthorized Access/Disclosure | Paper/Films |
| PurFoods, LLC | IA | Healthcare Provider | 1,229,333 | 08/25/2023 | Hacking/IT Incident | Network Server |
| Associates in Pediatric Dentistry | LA | Healthcare Provider | 9,703 | 08/25/2023 | Hacking/IT Incident | |
| Data Media Associates | GA | Business Associate | 74,730 | 08/24/2023 | Hacking/IT Incident | Other |
| Detroit Central City Community Mental Health | MI | Healthcare Provider | 1,412 | 08/24/2023 | Hacking/IT Incident | |
| IEC Group, Inc. dba AmeriBen | ID | Business Associate | 74,884 | 08/24/2023 | Unauthorized Access/Disclosure | |
| Milan Eye Center | GA | Healthcare Provider | 67,336 | 08/23/2023 | Hacking/IT Incident | Network Server |
| PRIME THERAPEUTICS LLC | MN | Business Associate | 6,050 | 08/23/2023 | Hacking/IT Incident | Network Server |
| Vecino Health Centers | TX | Healthcare Provider | 1,339 | 08/22/2023 | Hacking/IT Incident | Network Server |
| Serco Inc. Group Health Plan | VA | Health Plan | 10,140 | 08/22/2023 | Hacking/IT Incident | Network Server |
| Absolute Dental Services | NC | Business Associate | 10,037 | 08/21/2023 | Hacking/IT Incident | |
| McAlester Regional Health Center | OK | Healthcare Provider | 500 | 08/21/2023 | Hacking/IT Incident | Desktop Computer, Network Server |
| The University of Massachusetts Chan Medical School | MA | Business Associate | 134,394 | 08/21/2023 | Hacking/IT Incident | Network Server |
| Health Care Service Corporation | IL | Health Plan | 192,231 | 08/21/2023 | Hacking/IT Incident | Network Server |
| Illinois Department of Public Health | IL | Healthcare Provider | 126,000 | 08/18/2023 | Hacking/IT Incident | Network Server |
| Advanced Reproductive Health Center Ltd., d/b/a Chicago IVF | IL | Healthcare Provider | 2,603 | 08/18/2023 | Hacking/IT Incident | Network Server |
| UofL Health | KY | Healthcare Provider | 8,175 | 08/18/2023 | Hacking/IT Incident | Network Server |
| SouthCoast Medical Group, LLC | GA | Healthcare Provider | 501 | 08/17/2023 | Hacking/IT Incident | Network Server |
| Morris Hospital & Healthcare Centers | IL | Healthcare Provider | 248,943 | 08/17/2023 | Hacking/IT Incident | Network Server |
| The Harris Center for Mental Health and IDD | TX | Healthcare Provider | 599,367 | 08/17/2023 | Hacking/IT Incident | Network Server, Other |
| Blue Cross Blue Shield of Arizona | AZ | Health Plan | 47,485 | 08/17/2023 | Hacking/IT Incident | Network Server |
| SysInformation Healthcare Services, LLC | TX | Business Associate | 501 | 08/17/2023 | Hacking/IT Incident | Network Server |
| United Healthcare Services, Inc. Single Affiliated Covered Entity | CT | Health Plan | 527 | 08/17/2023 | Hacking/IT Incident | Network Server |
| Baesman Group, Inc. | OH | Business Associate | 24,757 | 08/17/2023 | Hacking/IT Incident | Network Server |
| SUNY at Buffalo School of Dental Medicine | NY | Healthcare Provider | 765 | 08/16/2023 | Hacking/IT Incident | Network Server |
| A-Family Dental Care Center PC | PA | Healthcare Provider | 2,800 | 08/16/2023 | Unauthorized Access/Disclosure | Network Server |
| Kennedy University Hospital, Inc. t/a Jefferson Health | NJ | Healthcare Provider | 4,140 | 08/15/2023 | Unauthorized Access/Disclosure | Other Portable Electronic Device |
| Performance Health Technology | OR | Business Associate | 1,750,000 | 08/15/2023 | Hacking/IT Incident | Network Server |
| University of Utah | UT | Health Plan | 3,914 | 08/15/2023 | Hacking/IT Incident | Network Server |
| Monocacy Valley Dental Brian K. Motz, DDS, PC | MD | Healthcare Provider | 4,000 | 08/15/2023 | Theft | Laptop |
| Nice Pak Products Inc., Health and Welfare Benefits Plan | NJ | Health Plan | 8,487 | 08/14/2023 | Hacking/IT Incident | Network Server |
| TRACT Radiology | MS | Business Associate | 7,810 | 08/14/2023 | Hacking/IT Incident | Network Server |
| VNS Health Plans | NY | Health Plan | 103,775 | 08/14/2023 | Hacking/IT Incident | Network Server |
| United Bankshares, Inc. | DC | Business Associate | 8,801 | 08/11/2023 | Hacking/IT Incident | Other |
| American National Group, LLC | TX | Health Plan | 47,711 | 08/11/2023 | Hacking/IT Incident | Network Server |
| Colorado Department of Health Care Policy & Financing | CO | Health Plan | 4,091,794 | 08/11/2023 | Hacking/IT Incident | Network Server |
| Three Crowns Park | IL | Healthcare Provider | 516 | 08/11/2023 | Hacking/IT Incident | |
| El Centro Del Barrio d/b/a CentroMed | TX | Healthcare Provider | 350,000 | 08/11/2023 | Hacking/IT Incident | Network Server |
| EMS Management and Consultants Inc | NC | Business Associate | 223,598 | 08/10/2023 | Hacking/IT Incident | Network Server |
| Coastal Orthopedics & Sports Medicine of Southwest Florida | FL | Healthcare Provider | 501 | 08/10/2023 | Hacking/IT Incident | Network Server |
| iTrust Wellness Group | SC | Healthcare Provider | 981 | 08/10/2023 | Hacking/IT Incident | |
| Allison Transmission Inc. Health Care Program for Hourly Employees / Wellness Program for Salaried Employees | IN | Business Associate | 5,330 | 08/10/2023 | Hacking/IT Incident | Network Server |
| Madera County | CA | Health Plan | 1,146 | 08/09/2023 | Unauthorized Access/Disclosure | |
| Virginia Dept. of Medical Assistance Services | VA | Health Plan | 423,824 | 08/09/2023 | Hacking/IT Incident | Network Server |
| Sovos Compliance LLC | MA | Business Associate | 4,563 | 08/08/2023 | Hacking/IT Incident | Network Server |
| Lurie Children’s Surgical Foundation | IL | Healthcare Provider | 1,997 | 08/08/2023 | Hacking/IT Incident | Network Server |
| Harris Eye Care | MI | Healthcare Provider | 6,267 | 08/08/2023 | Hacking/IT Incident | Network Server |
| Premera Blue Cross | WA | Health Plan | 33,212 | 08/08/2023 | Hacking/IT Incident | Network Server |
| Spinal and Sports Care Clinic PS | WA | Healthcare Provider | 1,100 | 08/08/2023 | Hacking/IT Incident | Network Server |
| Missouri Department of Social Services | MO | Health Plan | 739,884 | 08/07/2023 | Hacking/IT Incident | Network Server |
| Redwood Coast Regional Center | CA | Healthcare Provider | 1,345 | 08/07/2023 | Hacking/IT Incident | |
| Cranberry Township Emergency Medical Service | PA | Healthcare Provider | 1,247 | 08/07/2023 | Hacking/IT Incident | Network Server |
| Gary Motykie, M.D., a Medical Corporation | CA | Healthcare Provider | 3,400 | 08/05/2023 | Hacking/IT Incident | Desktop Computer, Network Server |
| Radius Global Solutions | MN | Business Associate | 600,794 | 08/04/2023 | Hacking/IT Incident | Network Server |
| Maximus, Inc. | VA | Business Associate | 932 | 08/04/2023 | Hacking/IT Incident | Network Server |
| Indiana University Health | IN | Health Plan | 21,383 | 08/04/2023 | Hacking/IT Incident | Network Server |
| Capital Neurological Surgeons | CA | Healthcare Provider | 1,769 | 08/04/2023 | Hacking/IT Incident | |
| Brigham and Women’s Hospital | MA | Healthcare Provider | 987 | 08/04/2023 | Unauthorized Access/Disclosure | Other |
| Unum Group SACE | TN | Health Plan | 531,732 | 08/03/2023 | Hacking/IT Incident | Network Server |
| Self-insured group health plans sponsored by the City of Dallas | TX | Health Plan | 30,253 | 08/03/2023 | Hacking/IT Incident | Network Server |
| Cognizant Technologies Solutions U.S. Corporation | TX | Business Associate | 7,313 | 08/03/2023 | Hacking/IT Incident | Network Server |
| Advanced Care Partners, LLC | GA | Healthcare Provider | 518 | 08/03/2023 | Unauthorized Access/Disclosure | |
| Plumbers Local 8 Health & Welfare Fund | MO | Health Plan | 4,790 | 08/02/2023 | Hacking/IT Incident | |
| Grane Supply, Inc. | PA | Healthcare Provider | 798 | 08/01/2023 | Unauthorized Access/Disclosure | |
| The Health Plan of West Virginia, Inc. | WV | Health Plan | 1,292 | 08/01/2023 | Hacking/IT Incident | Network Server |
These breaches highlight the critical need for robust cybersecurity measures in the healthcare industry, especially for organizations handling sensitive patient data. Please note that this is not an exhaustive list, and there are many more incidents occurring regularly.
If you’re looking for what to do after a data breach, check this federal website for a guide and step by step instructions.
HARD DRIVE DESTRUCTION FAQs
Is it true that data breaches can happen to anyone, even small businesses?
Absolutely, data breaches are an equal-opportunity threat. They don’t discriminate based on the size of your organization. In fact, small businesses can be particularly vulnerable due to limited resources for cybersecurity. It’s essential for all businesses, regardless of size, to prioritize data security to safeguard against potential breaches.
What’s the most effective way to protect my data from cyber threats?
Protecting your data requires a multi-faceted approach. Start by implementing robust cybersecurity measures, such as encryption, multi-factor authentication, and regular backups. Additionally, ensure that your employees are well-trained in recognizing and mitigating potential threats. A holistic strategy is your best defense against cyberattacks.
Can I rely solely on advanced security software to protect my data?
What should I do if a data breach occurs in my organization?
How can I convince my organization to invest in cybersecurity measures?
What happens when a hospital has a data breach?
What are the consequences of a healthcare data breach?
What is the hospital cyber attack August 2023?
What is the biggest healthcare data breach?
Related Content
Addressing the Data Breach Crisis: Comprehensive Solutions for a Safer Digital World
Addressing The Data Breach Crisis: Comprehensive Solutions For A Safer Digital World'...
Why Use a Permanent And Secure On Site Shredding Service?
By using permanent and secure on site shredding solutions, companies can protect...
Professional Data Disposal – Why You Need It!
When you’re managing classified material, you want to ensure proper data disposal...
Data Destruction for Health Service
Laws regarding data destruction in the healthcare industry are very strict and...